|
FYI
- Congratulations, cyber graduates! - This season millions of
students will graduate from a college or university with a degree in
their chosen field. This is a great milestone, and each and every
one of them is to be congratulated for the fortitude and focus it
took to earn their degrees.
https://www.scmagazine.com/home/opinion/executive-insight/congratulations-cyber-graduates/
Medical data breaches gain lawmakersí attention - A series of data
breaches involving the medical information of more than 20 million
has attracted the attention of Congress to write the organization
for more details.
https://www.scmagazine.com/home/security-news/data-breach/a-series-of-data-breaches-involving-the-medical-information-of-more-than-20-million-has-attracted-the-attention-of-congress/
Huge scope of Australia's new national security laws reveals itself
- The Australian Federal Police's hunt for journalists' working
files highlights more of the wide-ranging powers granted by the
controversial Assistance and Access Act.
https://www.zdnet.com/article/huge-scope-of-australias-new-national-security-laws-reveals-itself/
Audit says TVA fails to comply with new federal cyber security
measures - The Tennessee Valley Authority has failed to comply with
new federal cyber security rules for email and web sites, a new
audit shows.
https://www.timesfreepress.com/news/breakingnews/story/2019/jun/04/audit-says-tva-fails-comply-new-federal-cyber-security-measures/496013/
Watchdog: Current pipeline security plans weak on cybersecurity,
coordination - The Transportation Security Administration's plans
for pipeline security aren't keeping up with rising threats in
cyberspace, according to the Government Accountability Office.
https://fcw.com/articles/2019/06/05/tsa-pipeline-security.aspx
The Winners of the National Championship for Girls Go CyberStart
2019 - Congratulate the top three teams in each of the states and
find out which three teams scored the highest throughout the U.S.
https://medium.com/girls-go-cyberstart/the-winners-of-the-national-championship-for-girls-go-cyberstart-2019-d8586d9f2d37
Nuclear Energy Regulators Need to Bring on More Cyber Experts,
Watchdog Says - Cyberattacks on nuclear power stations on the rise,
and an aging workforce may soon leave the government struggling to
defend plants against the latest threats.
https://www.nextgov.com/cybersecurity/2019/06/nuclear-energy-regulators-need-bring-more-cyber-experts-watchdog-says/157545/
U.S. House passes bill that would require DHS to maintain cyber
hunt, IR teams - The U.S. House of Representatives yesterday passed
its own version of the DHS Cyber Incident Response Teams Act of
2019, which would require the Department of Homeland Security to
permanently maintain cyber hunt and incident response teams that
help prevent and mitigate attacks on federal agencies and the
private sector.
https://www.scmagazine.com/home/security-news/government-and-defense/tktktktktk-u-s-house-passes-bill-that-w/
Medical cybersecurity execs may have priorities misplaced, study - A
recent study sought out how the healthcare industry is dealing with
the increasing number of cyberattacks targeting patient data found
those charged with securing the data may have their priorities
misplaced.
https://www.scmagazine.com/home/health-care/medical-cybersecurity-execs-may-have-priorities-misplaced-study/
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
- Coffey Health System Agrees to $250,000 Settlement to Resolve
Alleged Violations of False Claims and HITECH Acts - Coffey Health
System has agreed to a $250,000 settlement with the U.S. Department
of Justice to resolve alleged violations of the False Claims and
HITECH Acts.
https://www.hipaajournal.com/coffey-health-system-agrees-to-250000-settlement-to-resolve-alleged-violations-of-false-claims-and-hitech-acts/
Collections firm breach exposes data on 7.7M LabCorp customers -
Data exposed could include names, credit card information and
medical providers, among other things. A security breach at a
third-party billing collections firm exposed the personal and
financial data on as many as 7.7 million LabCorp customers, the
medical testing giant said Tuesday.
https://www.cnet.com/news/collections-firm-breach-exposes-data-on-7-7m-labcorp-customers/
Travelersí photos stolen after CBP subcontractor breached - Photos
of travelers and vehicles crossing U.S. borders were taken from a
Customs and Border Patrol (CBP) subcontractor through a cyberattack,
the agency said Monday.
https://www.scmagazine.com/home/security-news/travelers-photos-stolen-after-cbp-subcontractor-breached/
Paradise lost: 1.1 million accounts exposed in 2018 breach of gaming
site Emuparadise - Over 1.1 million accounts managed by the retro
gaming website Emuparadise were exposed in a newly reported breach
that actually took place back on April 1, 2018.
https://www.scmagazine.com/home/security-news/data-breach/paradise-lost-1-1-million-accounts-exposed-in-2018-breach-of-gaming-site-emuparadise/
Shanghai Jiao Tong University exposed 8.4 TB of email data -
Independent researcher xxdesmus discovered 9.5 billion rows of email
metadata owned by Shanghai Jiao Tong University in a database that
didnít require authentication.
https://www.scmagazine.com/home/security-news/data-breach/independent-researcher-xxdesmus-discovered-9-5-billion-rows-of-email-metadata-owned-by-shanghai-jiao-tong-university/
Hack Brief: Hackers Stole a Border Agency Database of Traveler
Photos - In its rush to gather biometric data from travelers in the
US, Customs and Border Protection has apparently neglected basic
safeguards to protect it.
https://www.wired.com/story/hackers-stole-traveler-photos-border-agency-database/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
We continue covering some of the
issues discussed in the "Risk Management Principles for Electronic
Banking" published by the Basel Committee on Bank Supervision.
Board and Management Oversight
- Principle 9: Banks
should ensure that clear audit trails exist for all e-banking
transactions.
Delivery of financial services over the Internet can make it more
difficult for banks to apply and enforce internal controls and
maintain clear audit trails if these measures are not adapted to an
e-banking environment. Banks are not only challenged to ensure that
effective internal control can be provided in highly automated
environments, but also that the controls can be independently
audited, particularly for all critical e-banking events and
applications.
A bank's internal control environment may be weakened if it is
unable to maintain clear audit trails for its e-banking activities.
This is because much, if not all, of its records and evidence
supporting e-banking transactions are in an electronic format. In
making a determination as to where clear audit trails should be
maintained, the following types of e-banking transactions should be
considered:
1) The opening, modification or closing of a customer's account.
2) Any transaction with financial consequences.
3) Any authorization granted to a customer to exceed a limit.
4) Any granting, modification or revocation of systems access
rights or privileges.
Return to
the top of the newsletter
FFIEC IT SECURITY -
We continue our series on the FFIEC
interagency Information Security Booklet.
SECURITY CONTROLS -
IMPLEMENTATION - OPERATING SYSTEM ACCESS (Part 1 of 2)
Financial institutions must control access to system software
within the various network clients and servers as well as
stand-alone systems. System software includes the operating system
and system utilities. The computer operating system manages all of
the other applications running on the computer. Common operating
systems include IBM OS/400 and AIX, LINUX, various versions of
Microsoft Windows, and Sun Solaris. Security administrators and IT
auditors need to understand the common vulnerabilities and
appropriate mitigation strategies for their operating systems.
Application programs and data files interface through the operating
system. System utilities are programs that perform repetitive
functions such as creating, deleting, changing, or copying files.
System utilities also could include numerous types of system
management software that can supplement operating system
functionality by supporting common system tasks such as security,
system monitoring, or transaction processing.
System software can provide high-level access to data and data
processing. Unauthorized access could result in significant
financial and operational losses. Financial institutions must
restrict privileged access to sensitive operating systems. While
many operating systems have integrated access control software,
third - party security software is available for most operating
systems. In the case of many mainframe systems, these programs are
essential to ensure effective access control and can often integrate
the security management of both the operating system and the
applications. Network security software can allow institutions to
improve the effectiveness of the administration and security policy
compliance for a large number of servers often spanning multiple
operating system environments. The critical aspects for access
control software, whether included in the operating system or
additional security software, are that management has the capability
to:
! Restrict access to sensitive or critical system resources or
processes and have the capability, depending on the sensitivity to
extend protection at the program, file, record, or field level;
! Log user or program access to sensitive system resources
including files, programs, processes, or operating system
parameters; and
! Filter logs for potential security events and provide adequate
reporting and alerting capabilities.
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)20.3.5
Network-Related Threats
Most of the human
threats of concern to HGA originate from insiders. Nevertheless, HGA
also recognizes the need to protect its assets from outsiders. Such
attacks may serve many different purposes and pose a broad spectrum
of risks, including unauthorized disclosure or modification of
information, unauthorized use of services and assets, or
unauthorized denial of services.
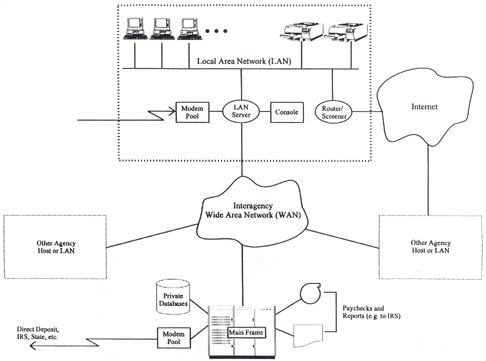
As shown in the figure
below, HGA's systems are connected to the three external networks:
(1) the Internet, (2) the Interagency WAN, and (3) the
public-switched (telephone) network. Although these networks are a
source of security risks, connectivity with them is essential to
HGA's mission and to the productivity of its employees; connectivity
cannot be terminated simply because of security risks.
In each of the past few
years before establishing its current set of network safeguards, HGA
had detected several attempts by outsiders to penetrate its systems.
Most, but not all of these, have come from the Internet, and those
that succeeded did so by learning or guessing user account
passwords. In two cases, the attacker deleted or corrupted
significant amounts of data, most of which were later restored from
backup files. In most cases, HGA could detect no ill effects of the
attack, but concluded that the attacker may have browsed through
some files. HGA also conceded that its systems did not have audit
logging capabilities sufficient to track an attacker's activities.
Hence, for most of these attacks, HGA could not accurately gauge the
extent of penetration.
In one case, an
attacker made use of a bug in an e-mail utility and succeeded in
acquiring System Administrator privileges on the server--a
significant breach. HGA found no evidence that the attacker
attempted to exploit these privileges before being discovered two
days later. When the attack was detected, COG immediately contacted
the HGA's Incident Handling Team, and was told that a bug fix had
been distributed by the server vendor several months earlier. To its
embarrassment, COG discovered that it had already received the fix,
which it then promptly installed. It now believes that no subsequent
attacks of the same nature have succeeded.
Although HGA has no
evidence that it has been significantly harmed to date by attacks
via external networks, it believes that these attacks have great
potential to inflict damage. HGA's management considers itself lucky
that such attacks have not harmed HGA's reputation and the
confidence of the citizens its serves. It also believes the
likelihood of such attacks via external networks will increase in
the future.
|