|
FFIEC
information technology audits
-
As a former bank examiner
with over 40 years IT audit experience, I will bring an examiner's
perspective to the FFIEC information technology audit for bankers in
Texas, New Mexico, Colorado, and Oklahoma.
For more information go
to
On-site FFIEC IT Audits.
FYI
- Is your organization meeting the cybersecurity “Standard of Care”?
- /CEOs and board members are increasingly under the microscope when
it comes to managing cyber risk. The financial, legal, and
regulatory impact that cyber incidents can have upon organizations
have transformed what was once an “IT problem” into a whole of
company challenge.
https://www.scmagazine.com/home/opinion/executive-insight/is-your-organization-meeting-the-cybersecurity-standard-of-care/
We ain't afraid of no 'ghost user': Infosec world tells GCHQ to
GTFO over privacy-busting proposals - Brit spies' idea would
backdoor WhatsApp et al without breaking the crypto - Bruce Schneier,
Richard Stallman and a host of western tech companies including
Microsoft and WhatsApp are pushing back hard against GCHQ proposals
that to add a "ghost user" to encrypted messaging services.
https://www.theregister.co.uk/2019/05/30/tech_hits_back_at_gchq_ghost_user_privacy_buster/
CEO who sold encrypted phones to criminal gangs gets nine years in
prison - Phantom Secure customers included the Sinaloa carter and
the Hells Angels biker gang.
https://www.zdnet.com/article/ceo-who-sold-encrypted-phones-to-criminal-gangs-gets-nine-years-in-prison/
The Marines' Top General Talks About A Changing Corps - Why did Bob
Neller join the Marines? "I needed a job," the top Marine officer
says nonchalantly. He went to Officer Candidate School the summer
before his senior year at the University of Virginia with the
intention of then going to law school.
https://www.npr.org/2019/06/04/729300525/the-marines-top-general-talks-about-a-changing-corps
Huawei ban revoked by science publisher IEEE - The Institute of
Electrical and Electronics Engineers on Sunday reversed restrictions
it had slapped on Huawei last week, letting the Chinese company's
scientists review its papers once again.
https://www.cnet.com/news/huawei-ban-revoked-by-science-publisher-ieee/
Organizations still struggle to manage vulnerability patches, report
- Nearly 27 percent of organizations worldwide have been breached as
a result of an unpatched vulnerability, according to Vulnerability
Management Survey.
https://www.scmagazine.com/home/security-news/vulnerabilities/organizations-still-struggle-to-manage-vulnerability-patches-report/
Premera Blue Cross reaches proposed $72M settlement with 2014 breach
victims - Health insurance company Premera Blue Cross has agreed to
a $72 million proposed settlement that would resolve a contentious
class-action lawsuit stemming from a 2014 data breach affecting
roughly 10.6 million people.
https://www.scmagazine.com/home/security-news/legal-security-news/premera-blue-cross-reaches-proposed-72m-settlement-with-2014-breach-victims/
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
-
Nonprofit People Inc. info exposed after two
employee email accounts breached - Nonprofit People Inc. has
notified nearly 1,000 of its current and former clients that
personal information was exposed after email accounts of two
employees had been breached.
https://www.scmagazine.com/home/security-news/data-breach/nonprofit-people-inc-info-exposed-after-two-employee-email-accounts-breached/
POS malware swipes payment info from Checkers and Rally’s
restaurants - Just over 100 Checkers and Rally’s fast food joints
and their customers were victimized by a long-running point-of-sale
malware campaign that stole payment card information from purchases
taking place as far back as December 2015, Checkers Drive-In
Restaurants announced in an online breach notification yesterday.
https://www.scmagazine.com/home/security-news/cybercrime/pos-malware-swipes-payment-info-from-checkers-and-rallys-restaurants/
Theta360 leak exposes 11 million photos, user data - An open
database exposed at least 11 million photographs after the Theta360
photo sharing system run by Ricoh was breached.
https://www.scmagazine.com/home/security-news/privacy-compliance/theta360-leak-exposes-11-million-photos-user-data/
Nonprofit People Inc. info exposed after two employee email accounts
breached - Nonprofit People Inc. has notified nearly 1,000 of its
current and former clients that personal information was exposed
after email accounts of two employees had been breached.
https://www.scmagazine.com/home/security-news/data-breach/nonprofit-people-inc-info-exposed-after-two-employee-email-accounts-breached/
Breach of bill collection agency may affect 11.9 million Quest
Diagnostics patients - Quest Diagnostics today disclosed that
roughly 11.9 million patients who sought medical testing through its
clinical labs may be affected by the breach of a third-party bill
collection agency.
https://www.scmagazine.com/home/security-news/breach-of-bill-collection-agency-may-affect-11-9-million-quest-diagnostics-patients/
ANU data breach exposes 19 years of staff and student data -
Australian National University revealed news of a data breach today
that took place in late 2018 compromising the PII of more than
200,000 employees and students who were associated with the school
for the last 19 years.
https://www.scmagazine.com/home/security-news/data-breach/anu-data-breach-exposes-19-years-of-staff-and-student-data/
UChicago Medicine secures database after publicly exposing info on
donors and patients - The University of Chicago Medicine scrambled
to secure a database containing information on patients as well as
existing and potential financial donors, after a researcher
discovered that a misconfiguration left nearly 1.68 million records
exposed to the public.
https://www.scmagazine.com/home/security-news/data-breach/uchicago-medicine-secures-database-after-publicly-exposing-info-on-donors-and-patients/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
We continue covering some of the
issues discussed in the "Risk Management Principles for Electronic
Banking" published by the Basel Committee on Bank Supervision.
Board and Management Oversight
- Principle 8: Banks
should ensure that appropriate measures are in place to protect the
data integrity of e-banking transactions, records and information.
Data integrity refers to the assurance that information that is
in-transit or in storage is not altered without authorization.
Failure to maintain the data integrity of transactions, records and
information can expose banks to financial losses as well as to
substantial legal and reputational risk.
The inherent nature of straight-through processes for e-banking
may make programming errors or fraudulent activities more difficult
to detect at an early stage. Therefore, it is important that banks
implement straight-through processing in a manner that ensures
safety and soundness and data integrity.
As e-banking is transacted over public networks, transactions are
exposed to the added threat of data corruption, fraud and the
tampering of records. Accordingly, banks should ensure that
appropriate measures are in place to ascertain the accuracy,
completeness and reliability of e-banking transactions, records and
information that is either transmitted over Internet, resident on
internal bank databases, or transmitted/stored by third-party
service providers on behalf of the bank. Common practices used to
maintain data integrity within an e-banking environment include the
following:
1) E-banking transactions should be conducted in a manner that
makes them highly resistant to tampering throughout the entire
process.
2) E-banking records should be stored, accessed and modified in
a manner that makes them highly resistant to tampering.
3) E-banking transaction and record-keeping processes should be
designed in a manner as to make it virtually impossible to
circumvent detection of unauthorized changes.
4) Adequate change control policies, including monitoring and
testing procedures, should be in place to protect against any
e-banking system changes that may erroneously or unintentionally
compromise controls or data reliability.
5) Any tampering with e-banking transactions or records should
be detected by transaction processing, monitoring and record keeping
functions.
Return to
the top of the newsletter
FFIEC IT SECURITY -
We continue our series on the FFIEC
interagency Information Security Booklet.
SECURITY CONTROLS -
IMPLEMENTATION -
NETWORK ACCESS
Firewall Policy (Part 3 of 3)
Financial institutions can reduce their vulnerability to these
attacks somewhat through network configuration and design, sound
implementation of its firewall architecture that includes multiple
filter points, active firewall monitoring and management, and
integrated intrusion detection. In most cases, additional access
controls within the operating system or application will provide an
additional means of defense.
Given the importance of firewalls as a means of access control,
good practices include:
! Hardening the firewall by removing all unnecessary services and
appropriately patching, enhancing, and maintaining all software on
the firewall unit;
! Restricting network mapping capabilities through the firewall,
primarily by blocking inbound ICMP traffic;
! Using a ruleset that disallows all traffic that is not
specifically allowed;
! Using NAT and split DNS (domain name service) to hide internal
system names and addresses from external networks (split DNS uses
two domain name servers, one to communicate outside the network, and
the other to offer services inside the network);
! Using proxy connections for outbound HTTP connections;
! Filtering malicious code;
! Backing up firewalls to internal media, and not backing up the
firewall to servers on protected networks;
! Logging activity, with daily administrator review;
! Using intrusion detection devices to monitor actions on the
firewall and to monitor communications allowed through the firewall;
! Administering the firewall using encrypted communications and
strong authentication, only accessing the firewall from secure
devices, and monitoring all administrative access;
! Limiting administrative access to few individuals; and
! Making changes only through well - administered change control
procedures.
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)20.3.5
Network-Related Threats
Most of the human
threats of concern to HGA originate from insiders. Nevertheless, HGA
also recognizes the need to protect its assets from outsiders. Such
attacks may serve many different purposes and pose a broad spectrum
of risks, including unauthorized disclosure or modification of
information, unauthorized use of services and assets, or
unauthorized denial of services.
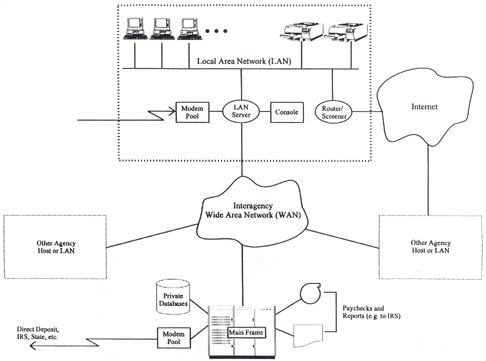
As shown in the figure
below, HGA's systems are connected to the three external networks:
(1) the Internet, (2) the Interagency WAN, and (3) the
public-switched (telephone) network. Although these networks are a
source of security risks, connectivity with them is essential to
HGA's mission and to the productivity of its employees; connectivity
cannot be terminated simply because of security risks.
In each of the past few
years before establishing its current set of network safeguards, HGA
had detected several attempts by outsiders to penetrate its systems.
Most, but not all of these, have come from the Internet, and those
that succeeded did so by learning or guessing user account
passwords. In two cases, the attacker deleted or corrupted
significant amounts of data, most of which were later restored from
backup files. In most cases, HGA could detect no ill effects of the
attack, but concluded that the attacker may have browsed through
some files. HGA also conceded that its systems did not have audit
logging capabilities sufficient to track an attacker's activities.
Hence, for most of these attacks, HGA could not accurately gauge the
extent of penetration.
In one case, an
attacker made use of a bug in an e-mail utility and succeeded in
acquiring System Administrator privileges on the server--a
significant breach. HGA found no evidence that the attacker
attempted to exploit these privileges before being discovered two
days later. When the attack was detected, COG immediately contacted
the HGA's Incident Handling Team, and was told that a bug fix had
been distributed by the server vendor several months earlier. To its
embarrassment, COG discovered that it had already received the fix,
which it then promptly installed. It now believes that no subsequent
attacks of the same nature have succeeded.
Although HGA has no
evidence that it has been significantly harmed to date by attacks
via external networks, it believes that these attacks have great
potential to inflict damage. HGA's management considers itself lucky
that such attacks have not harmed HGA's reputation and the
confidence of the citizens its serves. It also believes the
likelihood of such attacks via external networks will increase in
the future.
|