|
FYI
- Our cybersecurity testing meets
the independent pen-test requirements outlined in the FFIEC Information Security booklet. Independent pen-testing is part of any financial institution's cybersecurity defense.
To receive due diligence information, agreement and, cost saving fees,
please complete the information form at
https://yennik.com/forms-vista-info/external_vista_info_form.htm. All communication is kept strictly confidential.
FYI
- DDoS botnet makes slaves of your home and office routers -
Researchers have discovered a botnet which comprises of tens of
thousands of hijacked home routers. A massive DDoS botnet made up of
a slave network of hijacked home and office routers has been
revealed.
FYI
-
Russian hacking group was set to hit U.S. banks - A Russian hacking
group was poised to launch a cyber assault on U.S. banks, but may
have withdrawn those plans after being discovered.
http://thehill.com/policy/cybersecurity/241965-russian-hacking-group-was-set-to-hit-us-banks
FYI
-
Hack of airplane systems described in FBI docs raises security
questions - Claims and accusations continue to fly about security
researcher Chris Roberts's alleged tampering with airplane flight
control systems, with unsealed FBI warrants suggesting that Roberts
commandeered a plane briefly and experts questioning the veracity of
those assertions.
http://www.scmagazine.com/fbi-warrant-indicates-security-researcher-commandeered-plane-briefly/article/415361/
http://www.wired.com/2015/05/feds-say-banned-researcher-commandeered-plane/
FYI
-
Data breaches ‘increasing substantially’ - The rate of major data
breaches in the United States is rapidly increasing, as hackers
around the world become more sophisticated, a top FBI cyber official
said Thursday.
http://thehill.com/policy/cybersecurity/242110-fbi-official-data-breaches-increasing-substantially
FYI
- Employees acknowledge risky security behavior, continue to engage
in it - While most people acknowledge the security risks of opening
an email from an unknown sender or downloading an app from an
unauthorized app store, many continue to engage in this risky
behavior.
http://www.scmagazine.com/blue-coat-system-conducts-security-survey/article/415611/
FYI
- Federal prosecutors charge Chinese nationals with trade secret
theft - Over the weekend, federal agents arrested a Chinese
professor who had just entered the United States via a flight to Los
Angeles – one of six Chinese nationals charged with economic
espionage and theft of trade secrets from U.S. tech firms.
http://www.scmagazine.com/professor-other-chinese-nationals-indicted-on-32-counts/article/415887/
FYI
- How fear and self-preservation are driving a cyber arms race -
Silicon Valley is pouring more money into Internet security
companies than ever before. hen a man was fired from his job in
Minneapolis, Minn., last May, he inadvertently touched off a boom in
Silicon Valley.
http://www.cnet.com/news/how-fear-and-self-preservation-are-driving-a-cyber-arms-race/
FYI
- FTC gives thumbs up to companies that cooperate during breach
probes - The Federal Trade Commission (FTC) views a company “more
favorably” if it cooperates during the course of a data breach
investigation than one that doesn't, the commission said in a
Wednesday blog post.
http://www.scmagazine.com/ftc-gives-thumbs-up-to-companies-that-cooperate-during-breach-probes/article/416165/
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
-
Starbucks app targeted by hackers to drain bank accounts - Hackers
are believed to have been stealing money from people’s bank accounts
in the US using coffee giant Starbucks’ mobile app.
http://www.siliconrepublic.com/enterprise/item/42033-starbucks-app-targeted-by/
FYI
-
SEA hacks Washington Post mobile site - On Thursday, The Washington
Post's mobile website was hacked by the Syrian Electronic Army
(SEA), the same hacker collective that targeted the Post in an
August 2013 incident impacting several news sites.
http://www.scmagazine.com/sea-hacks-washington-post-mobile-site/article/415044/
FYI
-
Penn State breached by two threat actors, earliest attack in 2012 -
Penn State University is notifying roughly 18,500 individuals and
public and private research partners that their personal information
may have been compromised by two threat actors that were identified
on the College of Engineering network, one of who appears to be
based in China.
http://www.scmagazine.com/penn-state-breached-by-two-threat-actors-earliest-attack-in-2012/article/415037/
FYI
-
Three MetroHealth computers infected with malware, patients notified
- Ohio-based MetroHealth is notifying nearly 1,000 patients that
three computers in its Cardiac Cath Lab were infected with malware,
and the affected computers contained their personal information.
http://www.scmagazine.com/three-metrohealth-computers-infected-with-malware-patients-notified/article/415322/
FYI
-
Cyber extortionists targeting hedge funds - The government is
working with "several" hedge funds that have been victims of cyber
extortionists, said John Carlin, head of the Justice Department's
National Security Division.
http://www.usatoday.com/story/money/business/2015/05/08/hedge-funds-conference-cyber-espionage/26983845/
FYI
-
CareFirst
BlueCross BlueShield breached, more than one million individuals
notified - CareFirst BlueCross BlueShield is notifying more than one
million individuals that their personal information could have been
accessed by attackers who gained limited, unauthorized access to a
single CareFirst database in June 2014.
http://www.scmagazine.com/carefirst-tells-members-attackers-may-have-accessed-their-info/article/415879/
FYI
-
Cyberattack
on Penn State exposes passwords of 18K people - The university's
president apologizes for a "sophisticated" security breach that it
says involved an attack launched from China. Pennsylvania State
University's College of Engineering revealed Friday that it has been
the target of two "highly sophisticated" cyberattacks over the last
two years.
http://www.cnet.com/news/penn-state-cyberattack-exposes-passwords-from-18k-people/
FYI
-
UC Browser
found leaking personal data - UC Browser, the most popular mobile
web browser in China and India, contains multiple security and
privacy issues in both the English and Chinese versions of its
Android app.
http://www.scmagazine.com/researchers-investigate-uc-browsers-privacy-and-security/article/416129/
FYI
-
Telstra
discloses Pacnet security breach - Shortly after completing its
acquisition last month, Australia-based Telstra learned that an
unauthorized third party gained access to the corporate IT network
of data center operator Pacnet, according to post by Mike Burgess,
CISO of Telstra.
http://www.scmagazine.com/telstra-discloses-pacnet-security-breach/article/416109/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
OCC - Threats from
Fraudulent Bank Web Sites - Risk Mitigation and Response Guidance
for Web Site Spoofing Incidents (Part 5 of 5) Next week we will
begin our series on the Guidance on Safeguarding Customers
Against E-Mail and Internet-Related Fraudulent Schemes.
PROCEDURES TO ADDRESS SPOOFING - Contact the
OCC and Law Enforcement Authorities
If a bank is the target of a spoofing incident, it should promptly
notify its OCC supervisory office and report the incident to the FBI
and appropriate state and local law enforcement authorities. Banks
can also file complaints with the Internet Fraud Complaint Center
(see http://www.ic3.gov), a
partnership of the FBI and the National White Collar Crime Center.
In order for law enforcement authorities to respond effectively to
spoofing attacks, they must be provided with information necessary
to identify and shut down the fraudulent Web site and to investigate
and apprehend the persons responsible for the attack. The data
discussed under the "Information Gathering" section should meet this
need.
In addition to reporting to the bank's supervisory office and law
enforcement authorities, there are other less formal mechanisms that
a bank can use to report these incidents and help combat fraudulent
activities. For example, banks can use "Digital Phishnet" (http://www.digitalphishnet.com/),
which is a joint initiative of industry and law enforcement designed
to support apprehension of perpetrators of phishing-related crimes,
including spoofing. Members of Digital Phishnet include ISPs,
online auction services, financial institutions, and financial
service providers. The members work closely with the FBI, Secret
Service, U.S. Postal Inspection Service, Federal Trade Commission
(FTC), and several electronic crimes task forces around the country
to assist in identifying persons involved in phishing-type crimes.
Return to
the top of the newsletter
FFIEC IT SECURITY
-
We continue our coverage of the
FDIC's "Guidance on Managing Risks Associated With Wireless Networks
and Wireless Customer Access."
Part II. Risks Associated with Wireless Internet Devices
As wireless Internet devices become more prevalent in the
marketplace, financial institutions are adopting wireless
application technologies as a channel for reaching their customers.
Wireless Internet services are becoming available in major cities
across the United States. Through wireless banking applications, a
financial institution customer could access account information and
perform routine non-cash transactions without having to visit a
branch or ATM.
The wireless Internet devices available today present attractive
methods for offering and using financial services. Customers have
access to financial information from anywhere they can receive
wireless Internet access. Many of the wireless devices have built-in
encryption through industry-standard encryption methods. This
encryption has its limits based on the processing capabilities of
the device and the underlying network architecture.
A popular standard for offering wireless applications is through
the use of the Wireless Application Protocol (WAP). WAP is designed
to bring Internet application capabilities to some of the simplest
user interfaces. Unlike the Web browser that is available on most
personal computer workstations, the browser in a wireless device
(such as a cell phone) has a limited display that in many cases can
provide little, if any, graphical capabilities. The interface is
also limited in the amount of information that can be displayed
easily on the screen. Further, the user is limited by the keying
capabilities of the device and often must resort to many key presses
for simple words.
The limited processing capabilities of these devices restrict the
robustness of the encryption network transmissions. Effective
encryption is, by nature, processing-intensive and often requires
complex calculations. The time required to complete the encryption
calculations on a device with limited processing capabilities may
result in unreasonable delays for the device's user. Therefore,
simpler encryption algorithms and smaller keys may be used to speed
the process of obtaining access.
WAP is an evolving protocol. The most recent specification of WAP (WAP
2.0 - July 2001) offers the capability of encrypting network
conversations all the way from the WAP server (at the financial
institution) to the WAP client (the financial institution customer).
Unfortunately, WAP 2.0 has not yet been fully adopted by vendors
that provide the building blocks for WAP applications. Previous
versions of WAP provide encryption between the WAP client and a WAP
gateway (owned by the Wireless Provider). The WAP gateway then must
re-encrypt the information before it is sent across the Internet to
the financial institution. Therefore, sensitive information is
available at the wireless provider in an unencrypted form. This
limits the financial institution's ability to provide appropriate
security over customer information.
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)
20.4.1
General Use and Administration of HGA's Computer System
HGA's Computer
Operations Group (COG) is responsible for controlling,
administering, and maintaining the computer resources owned and
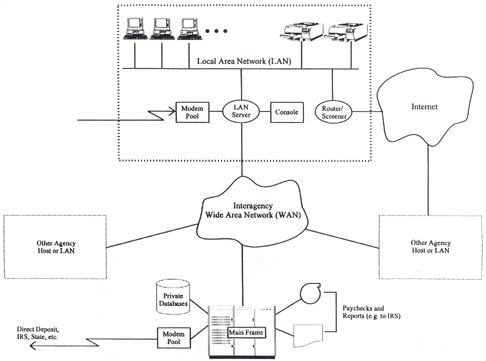
operated by HGA. These functions are depicted in Figure below
enclosed in the large, dashed rectangle. Only individuals holding
the job title System Administrator are authorized to establish
log-in ID's and passwords on multiuser HGA systems (e.g., the LAN
server). Only HGA's employees and contract personnel may use the
system, and only after receiving written authorization from the
department supervisor (or, in the case of contractors, the
contracting officer) to whom these individuals report.
COG issues copies of
all relevant security policies and procedures to new users. Before
activating a system account for new users, COG requires that they
(1) attend a security awareness and training course or complete an
interactive computer-aided-instruction training session and (2) sign
an acknowledgment form indicating that they understand their
security responsibilities.
Authorized users are
assigned a secret log-in ID and password, which they must not share
with anyone else. They are expected to comply with all of HGA's
password selection and security procedures (e.g., periodically
changing passwords). Users who fail to do so are subject to a range
of penalties.
Users creating data
that are sensitive with respect to disclosure or modification are
expected to make effective use of the automated access control
mechanisms available on HGA computers to reduce the risk of exposure
to unauthorized individuals. (Appropriate training and education are
in place to help users do this.) In general, access to
disclosure-sensitive information is to be granted only to
individuals whose jobs require it.
|
