|
FYI
- Our cybersecurity testing meets
the independent pen-test requirements outlined in the FFIEC Information Security booklet. Independent pen-testing is part of any financial institution's cybersecurity defense.
To receive due diligence information, agreement and, cost saving fees,
please complete the information form at
https://yennik.com/forms-vista-info/external_vista_info_form.htm. All communication is kept strictly confidential.
FYI
- US court says NSA phone data program is illegal - The US
government has long argued that the program is legal under the
controversial Patriot Act, but a federal appeals court sees things
differently. A US Appeals court has sent shockwaves through the
government and security industry after ruling that the National
Security Agency's wholesale collection of phone call data is
illegal.
http://www.cnet.com/news/us-court-says-nsa-phone-data-program-is-illegal/
FYI
- India and Japan form cyber alliance - Indian officials from the
Ministry of Telecom and the Department of Electronics and
Information Technology (DeitY) met with a visiting Japanese trade
delegation led by Minister of Economy and Trade Yoichi Miyazawa
according to the Economic Times.
http://www.scmagazine.com/japan-looks-to-invest-in-indias-it-sectors/article/412811/
FYI
- House approves controversial cybersecurity bill - The House of
Representatives passed bipartisan legislation on Wednesday designed
to help companies and the federal government better defend against
the growing threat of cyberattacks, despite opposition from privacy
advocates.
http://www.cnet.com/news/house-approves-controversial-cybersecurity-bill/
FYI
- Romanian rozzers round up alleged $15 MILLION ATM cybercrim gang -
25 people arrested over international cash-slurp operation -
Romanian police have arrested 25 people who are suspected of being
part of a cyber-crime gang that organised $15m in fraudulent bank
withdrawals.
http://www.theregister.co.uk/2015/04/28/romanian_police_arrest_25_15m_swindle_allegations/
FYI
- Twin brothers indicted on computer hacking charges - Twin brothers
in Virginia were indicted Thursday on computer hacking and other
charges.
http://www.scmagazine.com/twin-brothers-indicted-on-computer-hacking-charges/article/412825/
FYI
- A former Goldman Sachs programmer has been convicted for the
second time in four years on charges that he misused his former
employer’s code, adding a new chapter to an already bizarre and
controversial case that has drawn much unwanted attention to the
world of high-speed trading and elicited criticism of prosecutorial
overzealousness.
http://www.wired.com/2015/05/programmer-convicted-bizarre-goldman-sachs-caseagain/
FYI
- Lower house of French Parliament approves surveillance bill - The
lower house of the French Parliament has approved a controversial
intelligence bill that could broaden the government's surveillance
powers.
http://www.scmagazine.com/french-surveillance-bill-progresses-through-parliament/article/413032/
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
- Ryanair stung after $5m Shanghai'd from online fuel account -
Crooks siphoned off money from an account earmarked for the payment
of fuel bills via an electronic transfer to a bank in China last
week.
http://www.theregister.co.uk/2015/04/30/ryanair_online_heist/
FYI
- FBI investigating Rutgers University in DDoS attack - The FBI is
working with Rutgers University to identify the source of a series
of distributed denial-of-service (DDoS) attacks that have plagued
the school this week.
http://www.scmagazine.com/the-fbi-is-helpign-rutger-inveigate-a-series-of-ddos-attack/article/412149/
FYI
- Partners HealthCare says workers responded to phishing emails,
patient data at risk - Partners HealthCare Systems has published an
announcement on its website that personal and health-related data
belonging to its patients was potentially exposed to unauthorized
access.
http://www.scmagazine.com/partners-healthcare-group-patient-information-may-be-at-risk/article/412552/
FYI
- Oregon's Health CO-OP laptop stolen, about 15K members notified -
Oregon's Health CO-OP has notified approximately 15,000 current and
former members that a laptop containing personal information was
stolen.
http://www.scmagazine.com/oregons-health-co-op-laptop-stolen-about-15k-members-notified/article/412536/
FYI
- EllisLab server hacked, passwords possibly compromised - Hackers
last month gained unauthorized access to a server of software
development company EllisLab may have gotten their hands on personal
information belonging to EllisLab.com members, the company CEO Derek
Jones said in a Friday blog post.
http://www.scmagazine.com/attackers-use-stolen-login-info-to-hack-into-ellislabs-servers/article/412796/
FYI
- Possible payment card breach at Hard Rock Hotel & Casino Las Vegas
- Hard Rock Hotel & Casino Las Vegas is warning customers of a
potential security incident involving payment cards.
http://www.scmagazine.com/possible-payment-card-breach-at-hard-rock-hotel-casino-las-vegas/article/412819/
http://www.theregister.co.uk/2015/05/04/hard_rock_breach/
FYI
- Retail Capital notifies hundreds following security incident -
Michigan-based Retail Capital is notifying more than 700 individuals
that unauthorized access was gained to the electronic mailbox of a
sales manager, and personal information may have been compromised.
http://www.scmagazine.com/retail-capital-notifies-hundreds-following-security-incident/article/413042/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
OCC - Threats from
Fraudulent Bank Web Sites - Risk Mitigation and Response Guidance
for Web Site Spoofing Incidents (Part 3 of 5)
PROCEDURES TO ADDRESS SPOOFING - Information
Gathering
After a bank has determined that it is the target of a spoofing
incident, it should collect available information about the attack
to enable an appropriate response. The information that is
collected will help the bank identify and shut down the fraudulent
Web site, determine whether customer information has been obtained,
and assist law enforcement authorities with any investigation.
Below is a list of useful information that a bank can collect.
In some cases, banks will require the assistance of information
technology specialists or their service providers to obtain this
information.
* The means by which the bank became aware that it was the
target of a spoofing incident (e.g., report received through
Website, fax, telephone, etc.);
* Copies of any e-mails or documentation regarding other forms of
communication (e.g., telephone calls, faxes, etc.) that were used to
direct customers to the spoofed Web sites;
* Internet Protocol (IP) addresses for the spoofed Web sites
along with identification of the companies associated with the IP
addresses;
* Web-site addresses (universal resource locator) and the
registration of the associated domain names for the spoofed site;
and
* The geographic locations of the IP address (city, state,
and country).
Return to
the top of the newsletter
FFIEC IT SECURITY
-
We continue our coverage of
the FDIC's "Guidance
on Managing Risks Associated With Wireless Networks and Wireless
Customer Access."
PART I. Risks Associated with Wireless Internal Networks
Financial institutions are evaluating wireless networks as an
alternative to the traditional cable to the desktop network.
Currently, wireless networks can provide speeds of up to 11 Mbps
between the workstation and the wireless access device without the
need for cabling individual workstations. Wireless networks also
offer added mobility allowing users to travel through the facility
without losing their network connection. Wireless networks are also
being used to provide connectivity between geographically close
locations as an alternative to installing dedicated
telecommunication lines.
Wireless differs from traditional hard-wired networking in that it
provides connectivity to the network by broadcasting radio signals
through the airways. Wireless networks operate using a set of FCC
licensed frequencies to communicate between workstations and
wireless access points. By installing wireless access points, an
institution can expand its network to include workstations within
broadcast range of the network access point.
The most prevalent class of wireless networks currently available
is based on the IEEE 802.11b wireless standard. The standard is
supported by a variety of vendors for both network cards and
wireless network access points. The wireless transmissions can be
encrypted using "Wired Equivalent Privacy" (WEP) encryption. WEP is
intended to provide confidentiality and integrity of data and a
degree of access control over the network. By design, WEP encrypts
traffic between an access point and the client. However, this
encryption method has fundamental weaknesses that make it
vulnerable. WEP is vulnerable to the following types of decryption
attacks:
1) Decrypting information based on statistical analysis;
2) Injecting new traffic from unauthorized mobile stations
based on known plain text;
3) Decrypting traffic based on tricking the access point;
4) Dictionary-building attacks that, after analyzing about a
day's worth of traffic, allow real-time automated decryption of all
traffic (a dictionary-building attack creates a translation table
that can be used to convert encrypted information into plain text
without executing the decryption routine); and
5) Attacks based on documented weaknesses in the RC4
encryption algorithm that allow an attacker to rapidly determine the
encryption key used to encrypt the user's session).
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)
20.3.5 Network-Related
Threats
Most of the human
threats of concern to HGA originate from insiders. Nevertheless, HGA
also recognizes the need to protect its assets from outsiders. Such
attacks may serve many different purposes and pose a broad spectrum
of risks, including unauthorized disclosure or modification of
information, unauthorized use of services and assets, or
unauthorized denial of services.
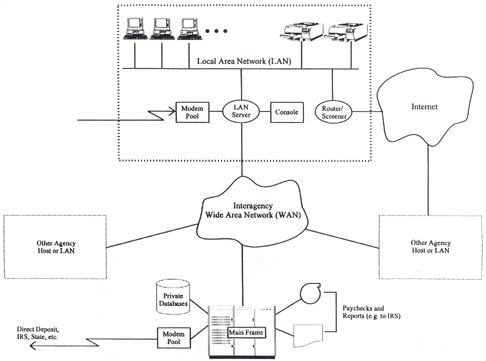
As shown in the figure
below, HGA's systems are connected to the three external networks:
(1) the Internet, (2) the Interagency WAN, and (3) the
public-switched (telephone) network. Although these networks are a
source of security risks, connectivity with them is essential to
HGA's mission and to the productivity of its employees; connectivity
cannot be terminated simply because of security risks.
In each of the past few
years before establishing its current set of network safeguards, HGA
had detected several attempts by outsiders to penetrate its systems.
Most, but not all of these, have come from the Internet, and those
that succeeded did so by learning or guessing user account
passwords. In two cases, the attacker deleted or corrupted
significant amounts of data, most of which were later restored from
backup files. In most cases, HGA could detect no ill effects of the
attack, but concluded that the attacker may have browsed through
some files. HGA also conceded that its systems did not have audit
logging capabilities sufficient to track an attacker's activities.
Hence, for most of these attacks, HGA could not accurately gauge the
extent of penetration.
In one case, an
attacker made use of a bug in an e-mail utility and succeeded in
acquiring System Administrator privileges on the server--a
significant breach. HGA found no evidence that the attacker
attempted to exploit these privileges before being discovered two
days later. When the attack was detected, COG immediately contacted
the HGA's Incident Handling Team, and was told that a bug fix had
been distributed by the server vendor several months earlier. To its
embarrassment, COG discovered that it had already received the fix,
which it then promptly installed. It now believes that no subsequent
attacks of the same nature have succeeded.
Although HGA has no
evidence that it has been significantly harmed to date by attacks
via external networks, it believes that these attacks have great
potential to inflict damage. HGA's management considers itself lucky
that such attacks have not harmed HGA's reputation and the
confidence of the citizens its serves. It also believes the
likelihood of such attacks via external networks will increase in
the future.
|
